EV Chargers Could Be A Serious Target For Hackers

Computers! They’re in everything these days. Everything from thermostats to fridges and even window blinds are now on the Internet, and that makes them all ripe for hacking.
Electric vehicle chargers are becoming a part of regular life. They too are connected devices, and thus pose a security risk if not designed and maintained properly. As with so many other devices on the Internet of Things, the truth is anything but.
Compromised!
Sometimes, securing a certain system or device is as easy as disconnecting it from the network. When it comes to light switches and door locks, for example, we got by perfectly fine for years without accessing them online. However, in the case of EV chargers, it’s not practical. At the very least, connectivity is required to run payment systems. Additionally, being able to monitor the status and health of EV chargers remotely is a big help in keeping them available and operational.
Given that EV chargers must be connected, securing them is important. However, research by Sandia National Laboratories indicates that thus far, EV charger companies haven’t done the best job at protecting their systems. Researchers investigated a variety of attack vectors and vulnerabilities and found many areas where existing systems were simply not up to scratch.
Vehicle-to-charger interfaces were studied as a primary target. EV chargers generally communicate with vehicles over signals passed through the charge cable. This communication involves negotiation on power levels and charge time, among other details. However, it could also be a path for malware to infect an EV charger if the vehicle’s responses aren’t handled properly or sanitized. Researchers found that not only could data be sniffed from these connections, but that a low-powered attack with a software-defined radio (SDR) could stop a vehicle’s charging session from up to 47 meters away. These interfaces are often completely unencrypted, too, leaving them vulnerable to man-in-the-middle and spoofing attacks.

The user interfaces of EV chargers are also vulnerable. The simplest attacks mirror those used at gas pumps, where card readers are fitted with skimmer devices to capture card data. Other straightforward hacks include RFID cloning attacks for systems that rely on those for payment and account management. The smartphone apps used by charging networks can also be a target for hackers.
Much like other network hardware like printers, EV chargers often come with web-based configuration interfaces. And, just like printers, many of these inevitably end up accessible on the wider internet. Researchers found all kinds of EV chargers that had their configuration pages publicly accessible. Even worse, many had very weak credentials, often being configured with basic passwords or only requiring a serial number for access.
Even if the web services are secured, admin interfaces were still found to pose a serious risk. Often, EV chargers come with some form of diagnostic and maintenance port. This can be via serial, WiFi, Ethernet, USB, or Bluetooth. In many cases, chargers were found to have unneeded services like Telnet and FTP accessible over these intefaces, presenting a broader security risk. In some cases, chargers would readily allow firmware dumps or unsigned updates to be made, or exfiltration of log data. Worse, in many cases, the physical ports were poorly secured, providing easy access to malicious actors.
Potential Consequences
Vulnerabilities in EV chargers can present a variety of consequences in the event a device is compromised. Many of those consequences are minor in nature and limited in their scope. For example, a charger fitted with a card skimmer could lead to a criminal compromising the credit cards of a few hundred users. Open web configuration pages could let a hacker disable chargers or cancel user’s sessions in progress.
However, in some cases, the consequences can be far greater. A charger with compromised firmware could potentially be configured to disable certain safety features, placing users at risk. Chargers could be reprogrammed to energise cables prior to their safe insertion, leading to a risk of electrocution. Spoofed vehicle-to-charger communications could lead to a charger delivering excessive power to the vehicle. In such a situation, a properly-secure vehicle may shut down the connection to a rogue charger. However, ideally, both the vehicle and the charger would be secure enough not to pose the risk in the first place.
There are larger-scale concerns, too. Modern EV chargers demand huge amounts of power from the grid. While home chargers of 7 kW and 11 kW were once the norm, today’s DC fast chargers run at power levels in excess of 350 kW. At those power levels, researchers fear there is potential to cause significant disruption to the power grid with the right attack. If an attacker could control enough vehicle chargers, simply getting them all to stop at once could threaten the frequency and voltage stability of the grid. At current levels of EV uptake, this isn’t a major risk. There simply aren’t enough vehicles placing enough load on the grid all at once to cause a threat.
However, as EV uptake rises, the threat increases. With vehicle-to-grid chargers becoming a thing, too, there is also the potential for an oscillating attack method. Huge numbers of vehicles suddenly demanding power from the grid, then seconds later attempting to feed power back in could make it difficult for authorities to maintain control over the power network. Controlling the power grid is all about balancing electricity generation with power demand from the grid. Sudden changes in demand and supply from an EV charger botnet could cause widespread blackouts and even temporarily drive certain infrastructure offline. Doing so would likely require control of hundreds of thousands of chargers near-simultaneously, though, so for now, power grid engineers can continue to sleep soundly at night.
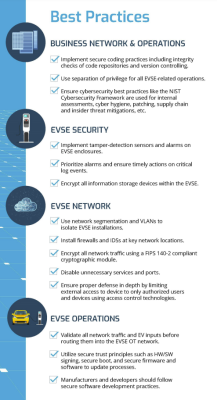
With EV charger rollouts only increasing in coming years, the time to get security right is now. Thankfully, Sandia National Laboratory has provided a document on best practices for the EV charger industry. Much of it is straightforward stuff, like physically securing admin ports, verifying firmware updates, and keeping web config interfaces behind strict firewalls. Having a list of best practices all in one place, though, is an easy way for companies to ensure their products aren’t unnecessarily insecure.
from Blog – Hackaday https://ift.tt/EJCnrRg
Comments
Post a Comment