What’s That AccessUSB Menu In My LG SmartTV?
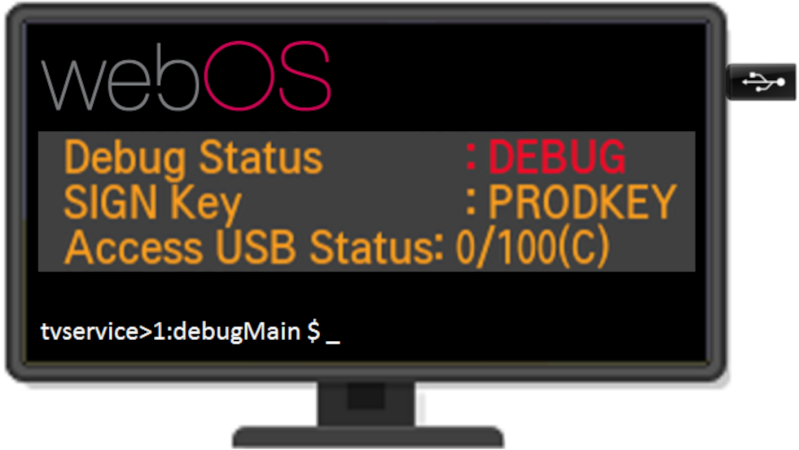
One boring evening, [XenRE] was looking through service menus on their LG Smart TV (Russian, Google Translate), such menus accessible through use of undocumented IR remote codes. In other words, a fairly regular evening. They noticed an “Access USB Status” entry and thought the “Access USB” part looked peculiar. A few service manuals hinted that there’s a service mode you could access with an adapter made out of two back-to-back PL2303 USB-UART adapters – a few female-female jumper wires later, serial prompt greeted our hacker, and entering ‘debug’ into the prompt responded with some text, among it, “Access USB is NOT opened!!!”.
[XenRE] found the WebOS firmware for the TV online, encrypted and compressed into a proprietary LG .epk format, but liberated with an open-source tool. A few modules referred to AccessUSB there, and one detour into investigating and explaining WebOS USB vendor lock-in implementation later, they programmed an STM32 with the same VID and PID as the mythical AccessUSB device found in relevant WebOS modules decompiled with IDA. By this point, AccessUSB could safely be assumed to be a service mode dongle. The TV didn’t quite start beeping in a different pattern as we’d expect in a sci-fi movie, but it did notify about a “new USB device” – and started asking for a 6-symbol service menu password instead of a 4-symbol one.
Another firmware module was loaded into IDA, this time, the module responsible for AccessUSB verification. Some password rate limiting, but also time- and number-of-uses limitations were found – apparently, implemented so that LG can limit AccessUSB use by service centers, since, you see, even repairability has to have means-testing. In the same vein, it was found that the AccessUSB dongle requires RSA2048 and RSA4096-certificate-based authentication – thus, the TV was reflashed with a different RSA2048 key, and hacking continued. In the end, the AccessUSB option in the service menus got successfully unlocked. What happened?
A whole lot of previously greyed-out options in the InStart and EzAdjust service menus became changeable. From the factory, your TV might have options accessible but locked or hidden, just like your laptop’s BIOS. Such options might be region lock toggles that limit content playback depending on volatile and senseless media sharing agreements, or the “DVR” ability that might be disabled to comply with a bullet point in a media conglomerate contract. Oh, and it gives you a root shell on the TV. [XenRE] left a lot of things untold and code un-shared, sadly, but the description of this journey is valuable enough on its own; and comments (Google Translate) under that post even have an ex-service technician reminisce about the good old times.
Smart TVs areYet Another Linux Computer You Own But Cannot Program, universally a net negative when it comes to repairability, eco-friendliness, and growth of new generations of hackers and engineers. It is not fair that such possibilities are locked behind a cryptography-enforced engineering mode. Not that it limits anyone except consumers – we’ve even seen leaked CIA exploits to turn your Smart TV into a remote microphone. One could design all the beautiful custom Raspberry Pi sticks to make our TVs all that much “smarter”, but maybe the solution is taking a hammer to it instead. The “USB-UART adapter and IDA” hammer, to be clear.
from Blog – Hackaday https://ift.tt/4Bzfiuo
Comments
Post a Comment